The Dark Web: What Is It and How To Access It - robertsthenly
You may have heard about this mysterious place on the Internet named the 'Oceanic abyss Web'. Interest in the deep web and unilluminated network arose following a a couple of shrill profile data leaks, a growing interest in online privacy, references in mainstream media, and the widely publicized FBI investigation into online marketplace Silk Road that open the extent of online drug trafficking.
But what is exactly the deep net? Well it's not actually a 'place' but rather anywhere other than the visible web that is crawled, indexed and accessed through and through golf links fetched by search engines like Google. The deep network is actually single times bigger than the indexed entanglement, and IT encompasses very much more than the illegal or otherwise questionable activities that it is often related with -- though there's certainly a lot of that going on, too. Let's start by clearing finished whatever of the confusion among the different price that tend to be thrown around while discussing the Net's subway system.
Note: This feature was originally promulgated on 05/20/2016. We accept amended it and bumped it atomic number 3 part of our #ThrowbackThursday initiative.
Grade-constructed Web, Deep WWW, Dark WWW
In unproblematic terms, the Surface Web is anything that a search engine can find away crawling golf links and characteristic content online, while the Deep Web is anything that a research locomotive can't find. The Dark Web on the other hand merely represents a smaller fortune of the low-pitched web that has been intentionally hidden and is inaccessible done classic web browsers.
To exemplify this a bit further, the deep web can in reality let in things like academic databases, which can be accessed through with a normal web browser but are not accessible to search engines.
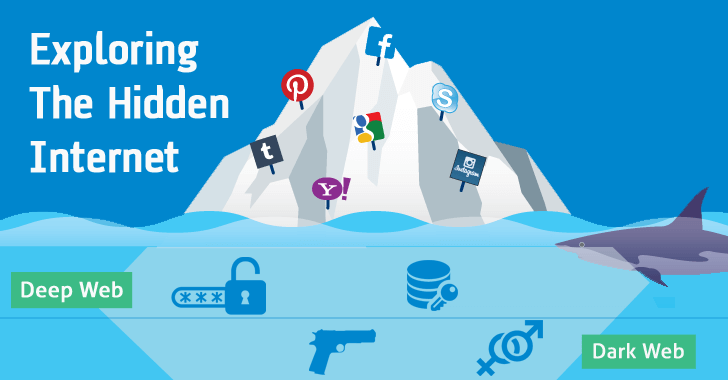
Information technology also includes content within mainstream websites that is simply non assemble to be accessed through a search engine. For example content posted on Facebook that is only available to the poster's friends, non the general public, operating room results for specific queries on a travel booking web site -- you merely can't sire to the content by clicking through with links like a explore engine would.
Accessing the Dark World Wide Web
The Tor web is the most ordinarily celebrated place where dark vane content resides. This anonymous network consists of thousands of servers settled all over the world run by volunteers and online privacy advocates. Its name is an acronym for 'The Allium cepa Router' in reference to its namesake routing technique, which creates a path through randomly assigned Tor servers, or nodes, before reaching whatever website you are visiting. During this process data packets are wrapped in successive layers of packets that get "stark naked sour" at each node until reaching the destination.
Here is a Thomas More field of study explanation, but in concise terms, the result is that no one node knows the complete path between your computer and a web site, only the last place the packet boat was, and the next place it will be. This makes it well-nig impossible for anyone to retrace the traffic back to you.
While finding content on the dark web bottom bring up time and plenty of patience, technically, accessing the Tor network International Relations and Security Network't that complicated at complete. You simply penury to download and install the Tor browser available for Windows, macOS, and Linux. IT is no different from installing any other piece of software program and it's very simple to use every bit IT's just a limited version of Firefox.
Protecting Yourself
If you'Re serious about the security of whatsoever IT is you're doing happening the dark World Wide Web, it's worth running an entirely separate surroundings from your intense computer and net connection. Tails OS is a bootable operating system that's already preconfigured to maximize privacy and that you can run from a USB stick or a virtual machine. Tails has an installation wizard that guides you gradual through the swear out of mise en scene improving the software so that shouldn't pose much of a challenge either. Tails received a caboodle of press when it was disclosed that Edward Snowden was using information technology to avoid NSA snooping. Its sole purpose is preserving your privacy and anonymity online by relying along the Tor network and other tools to keep down your activity secret.
Layering your localisation past starting at a random Wi-Fi hotspot and then connecting to a VPN before load Tor will greatly increase your betting odds of anonymity.
We have printed a more thorough, consecrate article to keeping yourself safe patc surfriding the small-seeded underbody of the web. You can read that Here.
What Will I Find Inside the Dark Web?
Almost any character of illegal and lawfully problematical products and services can be found in the seedier corners of the web. Unitary of the about prominent examples is the Silk Road, the now defunct online marketplace where you could score anything from drugs and throw them armored to you, lease a hitman, buy passports and charge card information, weapons -- you diagnose it. Several copycats take up sprung and destroyed since the Silk Road was taken down in 2013.
But flatbottom though technologies such as Tor are wont to help illegal activities, the technology itself isn't inherently good or bad. In fact, you might beryllium surprised to learn that Tor was created with financial subscribe from the US government as a instrument for bringing up majority rule in inhibitory regimes, and that's exactly what it's used for a lot of the time. Information technology's become popular with journalists and activists and even regular citizens who assess seclusion and freedom of formulation.
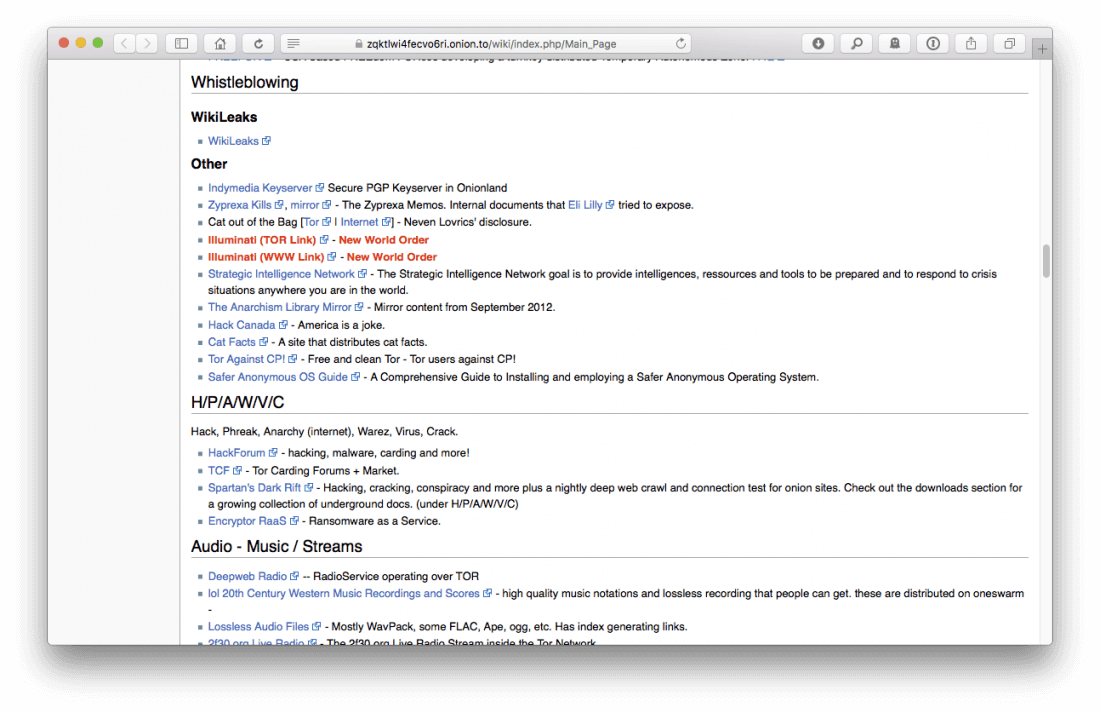
Where to Get Started Erst You're Inside
Finding content inside the deep or dark web is within reason reminiscent of the early days of the planetary wide entanglement before look for engines like Altavista and Google successful finding happy agency easier. You can traverse link directories like OnionDir and The Hidden Wiki which list sites under a range of categories covering various services and interests -- blogs, hosting, forums, warez, hacking, to name a few.
Thither are also a few search engines like DuckDuckGo and you can detect some guidance OR related information on reddit, too. There bequeath be a great deal of sites that have been taken land or are offline so finding employed, up-to-date links and directories can take some clip.
Nothing is 100% Anonymous or Secure
Even though the Tor web browser protects you by routing your traffic through various different Information science locations, and Tails OS includes built-in encoding, nothing is 100% faceless surgery secure. Tor and Tails' websites list a number of recommendations and best practices for remaining unnamed as best possible, equivalent using HTTPS versions of websites, avoiding web browser plugins or torrenting over Tor, and of course, non giving away personal inside information on websites you visit. We consume likewise written our own list of security recommendations here.
Finally, using Tor shouldn't perplex you in trouble with the authorities on its own but merely being a Tor user can arouse suspicion with the law. The unnamed mesh has longstanding been a target of government agencies like the NSA and the Federal Bureau of Investigation, which have with success First State-anonymized criminals before. So to be clear, if you are capable something illegal IT could land you in ratified trouble.
Source: https://www.techspot.com/article/1177-dark-web/
Posted by: robertsthenly.blogspot.com


0 Response to "The Dark Web: What Is It and How To Access It - robertsthenly"
Post a Comment